Mergers and acquisitions create many opportunities for organizations, but they are not without their challenges. One of these challenges is building a plan to merge the two computer networks. Intelligent NetFlow analysis can help with this effort.
Asset Discovery
One of the first steps in designing an effective migration plan is taking an inventory of the acquisition’s assets. By examining host records created by observing NetFlow, a single list of every host serving SMTP (email) can be resolved.
That returns a list of every active SMTP observed on the network.
These inventories can easily be created for every service the parent company provides, allowing engineers and architects to appropriately identify which servers need to be moved.
Service Profile
Different networks use network applications differently. A histogram of NetFlow records can reveal what kind of impact moving those services will have on the network.
Below is a snapshot of how the acquisition network is using the Internet links:
This is a breakdown of internal application use:
Columnar data can also be generated in short order. Here is the short list of Internet applications being used.
These reports can be tailored to reveal services provided to outside (Internet users), applications consumed and internal services.
Policy Violations
Prohibited services under the new policies can be resolved in short order. In the examples below, the use of P2P, Dropbox and Tunnel (i.e. onion routing) can be observed.
Using the host inventory, individual violators can be queried in the same manner that SMTP servers were found earlier.
Enforcement Success
In an earlier entry, I explained the importance of monitoring the effectiveness of network security mechanisms. NetFlow can easily display violations or security bypasses occurring in the evaluated network.
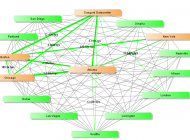
Link monitoring
In planning network expansion to allow for the integration of two networks, it is important to understand how different geographic locations send data. Building maps of those relationships can help.
Building capacity planning metrics off of those relationship maps can provide histograms of traffic patterns.
Security Checking
NetFlow analysis can prove to be an effective method for detecting security events including worm and botnet infections, as well as advanced threats currently active in the acquisition network.
Wrap Up
Intelligent NetFlow analysis can solve many problems associated with M&A. It provides detailed information on security events, policy violations, utilized services and capacity planning.
For further details on achieving network visibility with NetFlow, go to: http://www.lancope.com/solutions/.












