Network Behavioral Anomaly Detection, or NBAD, is an innovative approach to advanced threat detection that dates back to the year 2000. In an article published in 2004 on the Therminator project, Dr. John McEachen of the US Naval Postgraduate School states that NBAD methodologies have been based on the assumption that malicious network activity is inherently different from normal activity.
Traditional network threat detection models focus on pattern matching in communications. This approach has become known as “signature detection.” The limitation of signature based intrusion detection is that it requires knowledge of all network exploits. Recent research by Symantec Research Labs reveals that the time to craft these signatures can take months or years. This deficiency leaves networks vulnerable to many types of unknown threats for long periods of times.
NBAD is based on detection of bad traffic on the network without needing to know details around the exploit. As Dr. McEachen was working on the Therminator project at the US Naval Postgraduate School in 2001, Dr. John Copeland of Georgia Institute of Technology (Georgia Tech) had already invented the NBAD solution, the StealthWatch System. In the years to follow several other products would come to market with varying levels of NBAD development.
NBAD Detection Methods
There are two major categories of detection in NBAD: Behavioral and Anomaly. Behavioral detection looks for known bad communication patterns associated with a network host/node. Anomaly detection looks for deviation in established normal/good traffic patterns. Solutions that only perform behavioral detection (and no substantial anomaly detection) are generally classified as Network Behavioral Analysis (NBA) solutions. Tools that only perform anomaly detection (like Therminator) are labeled as Network Anomaly Detection (NAD) solutions.
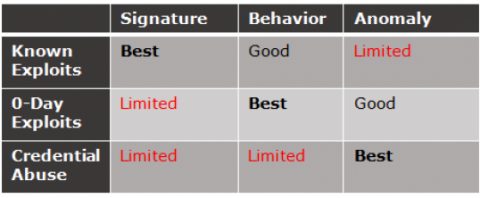
Below is a comparison of detection approaches and their general effectiveness against different types of threat detection.
NBAD Data sources
When NBAD solutions were first created, they relied on packet capture. This was the traditional approach for gathering information in intrusion detection systems (IDS.) By 2004, NetFlow export from routers and switches became a new source of data for NBAD researchers. Since NBAD does not generally rely on pattern matching as traditional IDS does, the data provided in NetFlow can be sufficient for providing analysis. This pivot in data collection allowed NBAD solutions to see much deeper into the network (down to core or access) that could not be plausibly collected in a pure probe architecture.
Important Events in NBAD History
From 2000 to 2004, NBAD was largely limited to deployments in the US Federal space. At that time only the most innovative Enterprise security teams adopted NBAD into security operations.
By 2005, consensus in Enterprise InfoSec was that the threat of loss to advanced threats protected by NBAD were minimal and the cost of deploying and maintaining NBAD was high. This led to negligible adoption until 2009. This led many NBAD vendors and researchers to discontinue their efforts. Others focused on providing additional uses of NetFlow to Enterprise (such as Network Performance Monitoring/NPM.)
Around 2009, metrics on losses caused by cybercrime refueled discussions on advanced threat discussion methodologies including NBAD.
In 2013, Mandiant released a report attributing attacks against US Enterprise to the Chinese People’s Liberation Army. This further fueled discussions around the need for advanced threat detection as corporations added State Sponsored attackers to the list of threats against their companies.
Wrap Up
Lancope has been leading the charge in NBAD research since 2000. The StealthWatch System is the world’s leading NBAD technology. NBAD is a venerable technology that came to the InfoSec scene many years ahead of its time. In 2014, Enterprise security operations are waking to the same horrors that faced US Department of Defense researchers 14 years ago: the attacks are dangerous and traditional detection mechanisms are insufficient to detect them. NBAD has hit the mainstream.

